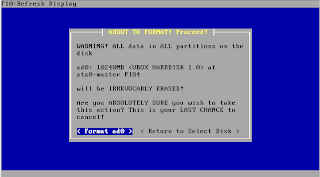
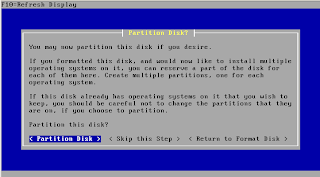
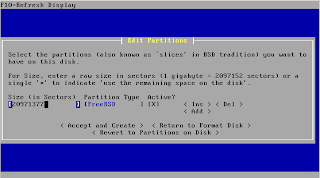
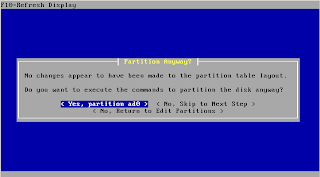
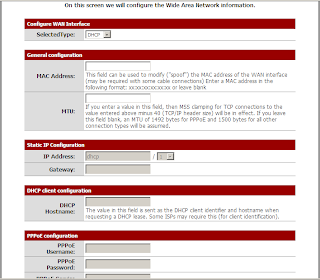
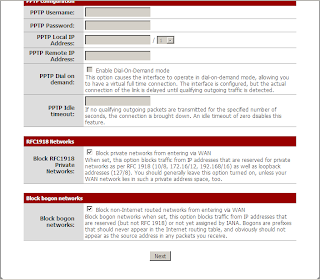
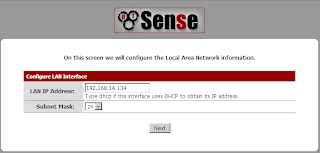
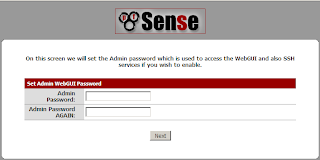
CPU / Memory
1. HPUX
2. AIX
3. Solaris
4. Linux
5. Tru64
HPUX
How to check CPU/Memory usage
# glance OR top OR vmstat OR iostat OR sar
## to check CPU/Memory utilisation
· Find large processes which currently filled up the CPU/Memory usage.
AIX
How to check CPU/Memory usage:
# sar OR vmstat OR iostat OR topas ## to check CPU/Memory utilisation
· Find large processes which currently filled up the CPU/Memory usage.
SOLARIS
How to check CPU/Memory usage:
# sar OR vmstat OR iostat ## to check CPU/Memory utilisation
· Find large processes which currently filled up the CPU/Memory usage.
LINUX
How to check CPU/Memory usage:
# sar OR vmstat OR iostat OR top ## to check CPU/Memory utilisation
· Find large processes which currently filled up the CPU/Memory usage.
TRU64
How to check CPU/Memory usage:
# vmstat OR iostat OR top ## to check CPU/Memory utilisation
· Find large processes which currently filled up the CPU/Memory usage.
HPUX
How to check disk space: (using /var as example)
# bdf /var
# find /var -xdev -type f -size +5000000c -exec ls -l {} \; | sort -nk 5
AIX, SOLARIS, LINUX, TRU64
How to check disk space:
# df -k /var
# find /var -xdev -type f -size +5000000c -exec ls -l {} \; | sort -nk 5
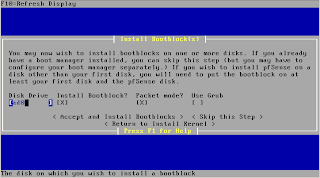
HPUX/AIX/SOLARIS/LINUX/TRU64
Pre-checking before reboot
Capture the system details
# bdf > /tmp/bdf.txt ## For HPUX
OR
# df –k > /tmp/df.txt ## For other OS
# netstat –in > /tmp/netstat.in.txt
# netstat –rn > /tmp/netstat.rn.txt
# lanscan > /tmp/lanscan.txt ## For HPUX
# ioscan –fn > /tmp/ioscan.txt ## For HPUX
# ps –ef | grep –i sap ## Double confirm no SAP running
# ps –ef | grep –I oracle ## Double confirm no Database running
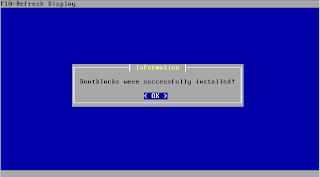
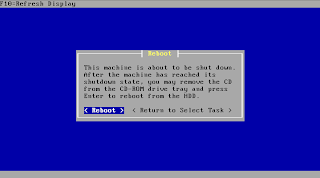
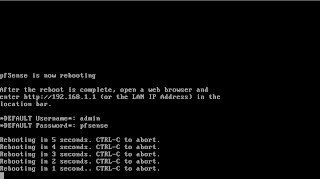
How to reboot server
# shutdown [-option] [ +Time [ Message ] ] ## man shutdown to find more the option
Account Creation
# finger
OR
# grep –i <> /etc/passwd
HPUX/AIX/SOLARIS/LINUX/TRU64
# useradd –c
## man useradd for more the option
AIX
# mkuser ## man mkuser for more the option
Account Mod
Do initial checking on the account
# finger
OR
# grep –i <> /etc/passwd
HPUX/SOLARIS/LINUX/TRU64
# usermod ## man usermod for more the option
AIX
# chuser ## man chuser for more the option
Account Deletion
Do initial checking on the account
# finger
OR
# grep –i <> /etc/passwd
HPUX/SOLARIS/LINUX/TRU64
# userdel –r
AIX
# rmuser ## man rmuser for more the option
Generic Process to add printer
1) Confirm details provided (such as printer queue name, IP address and model).
2) Perform initial checking:-
# ping
# lpstat –o
Issue following command to create print queue.
# hppi or sam ## HP UX
# smitty ## IBM
Generic Process to modify printer:
1) Confirm details provided (such as printer queue name, IP address and model).
2) Perform initial checking:-
HPUX
# ping
# lpstat –o
# grep –i model /etc/lp/interface ## Check printer model
# grep –i periph /etc/lp/interface ## Check printer IP
# grep –i
IBM
# Smitty
Issue following command to modify printer queue IP or model. Printer modify can be do anytime.
HPUX
# vi /etc/lp/interface ## Change network printer IP only
**To modify printer model, remove old print queue and recreate with new model.
**If print queue are remote printer, remove old print queue and recreate with new IP or model.
IBM
**Remove old print queue and recreate with new IP or model
Generic Process to delete printer:
1) Confirm details provided (such as printer queue name, IP address and model).
2) Perform initial checking:-
HPUX/IBM/SUN SOLARIS/Linus/Tru64
# ping
# lpstat –o
Issue following command to delete printer queue IP or model.
HPUX
# hppi or sam
IBM
# smitty